thanks to the help of numerous folks on the intertoobs!!!
Duh...I should have known this...but i'm impatient
http://forum.soft32.com/linux2/dsniff-make-error-ftopict43253.html
These patches really helped out
http://www.enzotech.net/dsniff.html
Thursday, July 30, 2009
Wednesday, July 29, 2009
Installing DSNIFF on centos is a full time job
glib2 this, libnids that, 5 different devel libs...hey it's free software what am i complain'n about
DSNIFF and SSL

I found this very informative site that walks one through the details of setting up a MITM rig to decompose SSL traffic. Exactly what I was looking for since busybox was not being nice to me.
http://forums.remote-exploit.org/tutorials-guides/9011-sniffing-ssl-traffic-using-mitm-attack-ettercap-fragrouter-webmitm-dnsspoof.html
(I think blogspot filters URLS with HTML tags), the above wouldn't show up....prolly because it's got the word EXPLOIT in it.)
Seems simple enough...just gonna take some time setting all this crap up, I love this stuff though and that's why I'm doing it.
In the mean time, I wanted to set up something to capture all the traffic to/from the router and I was looking at various firewalls etc...I finally settled on centos as a transparent bridge. One interface to the router, one to my switch, and Oreo stuffing in between.
If you want to do this yourself...it's DIRT SIMPLE, here's my rc.local script to get it going.
#!/bin/sh
brctl addbr br0
brctl addif br0 eth0
brctl addif br0 eth1
ip link set br0 up
ifconfig br0 192.168.0.3 netmask 255.255.255.0
route add default gw 192.168.0.1 dev br0
btw I'm running this on a 8 year old box I found in my basement under some paint rags. Aside from the oily smell the packets flow just fine.
busy box, applet not found
Since I managed to create some mips64 binaries and managed to get them on the router's filesystem, I thought I was in a good place....NOT. Apparently busybox (I didn't know this until now), is configured to only run the built in applets. It seems they actually turned off (at compile time) the ability to run arbitrary code via busybox. HOWEVER this certainly doesn't mean I couldn't upload my own firmware...there are at least 3 ways to do this...BUT I don't want to tank my rounter....so on to other ideas....like dsniff
Sunday, July 26, 2009
It's only a matter of time
Discovered open port 4567/tcp on x.y.235.2
Discovered open port 4567/tcp on x.y.235.3
Discovered open port 4567/tcp on x.y.235.134
Discovered open port 4567/tcp on x.y.235.201
Discovered open port 4567/tcp on x.y.235.202
Discovered open port 4567/tcp on x.y.235.204
Discovered open port 4567/tcp on x.y.235.205
Discovered open port 4567/tcp on x.y.235.207
Discovered open port 4567/tcp on x.y.235.208
Discovered open port 4567/tcp on x.y.235.206
Discovered open port 4567/tcp on x.y.235.216
Discovered open port 4567/tcp on x.y.235.217
Discovered open port 4567/tcp on x.y.235.219
Discovered open port 4567/tcp on x.y.235.220
Discovered open port 4567/tcp on x.y.235.221
Discovered open port 4567/tcp on x.y.235.222
Discovered open port 4567/tcp on x.y.235.224
Discovered open port 4567/tcp on x.y.235.226
Discovered open port 4567/tcp on x.y.235.225
Discovered open port 4567/tcp on x.y.235.227
Discovered open port 4567/tcp on x.y.235.228
Discovered open port 4567/tcp on x.y.235.229
Discovered open port 4567/tcp on x.y.235.231
Discovered open port 4567/tcp on x.y.235.230
Discovered open port 4567/tcp on x.y.235.215
Discovered open port 4567/tcp on x.y.235.179
Discovered open port 4567/tcp on x.y.235.232
Discovered open port 4567/tcp on x.y.235.233
Discovered open port 4567/tcp on x.y.235.235
Discovered open port 4567/tcp on x.y.235.236
Discovered open port 4567/tcp on x.y.235.234
Discovered open port 4567/tcp on x.y.235.237
Discovered open port 4567/tcp on x.y.235.239
Discovered open port 4567/tcp on x.y.235.240
Discovered open port 4567/tcp on x.y.235.238
Discovered open port 4567/tcp on x.y.235.242
Discovered open port 4567/tcp on x.y.235.251
Discovered open port 4567/tcp on x.y.235.253
Discovered open port 4567/tcp on x.y.235.252
Discovered open port 4567/tcp on x.y.235.254
Discovered open port 4567/tcp on x.y.235.3
Discovered open port 4567/tcp on x.y.235.134
Discovered open port 4567/tcp on x.y.235.201
Discovered open port 4567/tcp on x.y.235.202
Discovered open port 4567/tcp on x.y.235.204
Discovered open port 4567/tcp on x.y.235.205
Discovered open port 4567/tcp on x.y.235.207
Discovered open port 4567/tcp on x.y.235.208
Discovered open port 4567/tcp on x.y.235.206
Discovered open port 4567/tcp on x.y.235.216
Discovered open port 4567/tcp on x.y.235.217
Discovered open port 4567/tcp on x.y.235.219
Discovered open port 4567/tcp on x.y.235.220
Discovered open port 4567/tcp on x.y.235.221
Discovered open port 4567/tcp on x.y.235.222
Discovered open port 4567/tcp on x.y.235.224
Discovered open port 4567/tcp on x.y.235.226
Discovered open port 4567/tcp on x.y.235.225
Discovered open port 4567/tcp on x.y.235.227
Discovered open port 4567/tcp on x.y.235.228
Discovered open port 4567/tcp on x.y.235.229
Discovered open port 4567/tcp on x.y.235.231
Discovered open port 4567/tcp on x.y.235.230
Discovered open port 4567/tcp on x.y.235.215
Discovered open port 4567/tcp on x.y.235.179
Discovered open port 4567/tcp on x.y.235.232
Discovered open port 4567/tcp on x.y.235.233
Discovered open port 4567/tcp on x.y.235.235
Discovered open port 4567/tcp on x.y.235.236
Discovered open port 4567/tcp on x.y.235.234
Discovered open port 4567/tcp on x.y.235.237
Discovered open port 4567/tcp on x.y.235.239
Discovered open port 4567/tcp on x.y.235.240
Discovered open port 4567/tcp on x.y.235.238
Discovered open port 4567/tcp on x.y.235.242
Discovered open port 4567/tcp on x.y.235.251
Discovered open port 4567/tcp on x.y.235.253
Discovered open port 4567/tcp on x.y.235.252
Discovered open port 4567/tcp on x.y.235.254
CPE Wan Management Protocol v1.1
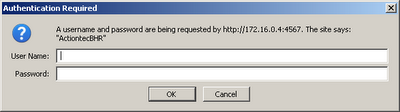
Well I think I found out what port 4567 is supposed to be for:
"2.3.4 Asynchronous ACS Initiated Sessions
An important aspect of service auto-configuration is the ability for the ACS to inform the CPE of a configuration change asynchronously. This allows the auto-configuration mechanism to be used for services that require near-real-time reconfiguration of the CPE. For example, this may be used to provide an end-user with immediate access to a service or feature they have subscribed to, without waiting for the next periodic contact.
The CPE WAN Management Protocol incorporates a mechanism for the ACS to issue a Connection Request to the CPE at any time, instructing it to establish a communication session with the ACS.
While the CPE WAN Management Protocol also allows polling by the CPE in lieu of ACS-initiated connections, the CPE WAN Management Protocol does not rely on polling or establishment of persistent connections from the CPE to provide asynchronous notification.
The basic mechanism defined in the CPE WAN Management Protocol to enable asynchronous ACS initiated communication assumes direct IP addressability of the CPE from the ACS. An alternative mechanism is defined in Annex G, which accommodates CPE operating behind a NAT gateway that are not directly addressable by the ACS."
"2.3.4 Asynchronous ACS Initiated Sessions
An important aspect of service auto-configuration is the ability for the ACS to inform the CPE of a configuration change asynchronously. This allows the auto-configuration mechanism to be used for services that require near-real-time reconfiguration of the CPE. For example, this may be used to provide an end-user with immediate access to a service or feature they have subscribed to, without waiting for the next periodic contact.
The CPE WAN Management Protocol incorporates a mechanism for the ACS to issue a Connection Request to the CPE at any time, instructing it to establish a communication session with the ACS.
While the CPE WAN Management Protocol also allows polling by the CPE in lieu of ACS-initiated connections, the CPE WAN Management Protocol does not rely on polling or establishment of persistent connections from the CPE to provide asynchronous notification.
The basic mechanism defined in the CPE WAN Management Protocol to enable asynchronous ACS initiated communication assumes direct IP addressability of the CPE from the ACS. An alternative mechanism is defined in Annex G, which accommodates CPE operating behind a NAT gateway that are not directly addressable by the ACS."
Saturday, July 25, 2009
unobscure_str
I found obscure_str's friend....
00000000001110f0 -31104(gp) 000000000000f0c0 000000000000f0c0 FUNC UND unobscure_str
Hmmm...wonder if
char *clearstr = malloc(1024);
clearstr = unobscure_str("&cc;Ya&b9;&ae;&19;]&d1;&be;&ba;v");
would give us an neato answer... IDA Pro...do you have any ideas?
00000000001110f0 -31104(gp) 000000000000f0c0 000000000000f0c0 FUNC UND unobscure_str
Hmmm...wonder if
char *clearstr = malloc(1024);
clearstr = unobscure_str("&cc;Ya&b9;&ae;&19;]&d1;&be;&ba;v");
would give us an neato answer... IDA Pro...do you have any ideas?
OpenRG lib
now that i have some mips64 binutils I can check out all the symbols in the openrg libraries...check these out
311: 000000000000b49c 0 FUNC GLOBAL DEFAULT 7 NtPasswordHash
371: 000000000000b3c4 0 FUNC GLOBAL DEFAULT 7 LmPasswordHash
0000000000110e50 -31776(gp) 000000000000f3c0 000000000000f3c0 FUNC UND obscure_str
hmmm obscure_str...wonder what that does????
311: 000000000000b49c 0 FUNC GLOBAL DEFAULT 7 NtPasswordHash
371: 000000000000b3c4 0 FUNC GLOBAL DEFAULT 7 LmPasswordHash
0000000000110e50 -31776(gp) 000000000000f3c0 000000000000f3c0 FUNC UND obscure_str
hmmm obscure_str...wonder what that does????
OK, now I've got gcc built...I guess I need to get the runtime installed.
[root@big binutils-2.19]# /usr/local/mips64-elf/bin/mips64-elf-gcc -v
Using built-in specs.
Target: mips64-elf
Configured with: ./configure --prefix=/usr/local/mips64-elf --target=mips64-elf --with-mpfr=/usr/local --with-gnu-as --with-gnu-ld --enable-languages=c,c++ --program-prefix=mips64-elf-
Thread model: single
gcc version 4.4.1 (GCC)
[root@big binutils-2.19]# /usr/local/mips64-elf/bin/mips64-elf-gcc -v
Using built-in specs.
Target: mips64-elf
Configured with: ./configure --prefix=/usr/local/mips64-elf --target=mips64-elf --with-mpfr=/usr/local --with-gnu-as --with-gnu-ld --enable-languages=c,c++ --program-prefix=mips64-elf-
Thread model: single
gcc version 4.4.1 (GCC)
Full Spectrum Dominance
A friend asked, out of curiosity, why I was researching this topic... I was concerned that the open port (4567) could lead to malicious use of the router by those outside the U.S government and law enforcement. Specifically countries like North Korea who have been rumored to deploy large bot nets in order to cause wide scale denial of service attacks across the global information grid as well as China who has been reported as having hacked into many U.S. Government networks. If the default password for port 4567 is not changed it could lead to wide spread misuse, not just by foreign state sponsored entities but also by crime syndicates like those operating out of Eastern Europe, Russia, South America and even those within the continental U.S. Especially alarming is that this seems to be the default configuration on all Fios enabled ISP provided home gateway/routers. My bandwidth up is 20Mbps. Imagine having hundreds or possibly thousands of these nodes under the full control of an enemy of the state. The fact that the operating system is Linux 2.6 adds more to my concern because it is quite simple to write custom tools and scripts that would execute whatever code the malicious user wishes. There are hundreds of API libraries available for Linux and the complexity of the tools that could be written makes this apparent flaw even more noteworthy. The ability to compose custom network packets and the high bandwidth available are really the top two concerns. Another one of my friends understands the gravity of this situation, this blog is hopefully going to get some attention so the problem gets addressed.
Interesting strings
It's taking me a lot longer than expected to get the cross compiler built...so I grabbed all the binaries off the router. One that stuck out was the openrg binary and some interesting strings I noticed:
Error creating maximum security rule
Aladdin
http://www2.jungo.com/~yoavp/mail_filter_pop3_server?vendor_id=%s&box_id=%s
http://www2.jungo.com/~oferfa/mail_filter_demo.htm?vendor_id=%s&box_id=%s
http://www2.jungo.com/~yoavp/mail_filter_expiry?vendor_id=%s&box_id=%s
http://www2.jungo.com/~yoavp/mail_filter_smtp_server?vendor_id=%s&box_id=%s
Not sure what those web sites are...but this really seems odd.
Here are some others
https://cpe-ems79.verizon.com/cwmpWeb/CPEMgt
https://upgrade.actiontec.com/
https://controlpanel.tzo.com/cgi-bin/tzopanel.exe
https://upgrade.actiontec.com/MI424WR2/MI424WR2.rmt
https://cpe-ems79.verizon.com/cwmpWeb/CPEMgt
Error creating maximum security rule
Aladdin
http://www2.jungo.com/~yoavp/mail_filter_pop3_server?vendor_id=%s&box_id=%s
http://www2.jungo.com/~oferfa/mail_filter_demo.htm?vendor_id=%s&box_id=%s
http://www2.jungo.com/~yoavp/mail_filter_expiry?vendor_id=%s&box_id=%s
http://www2.jungo.com/~yoavp/mail_filter_smtp_server?vendor_id=%s&box_id=%s
Not sure what those web sites are...but this really seems odd.
Here are some others
https://cpe-ems79.verizon.com/cwmpWeb/CPEMgt
https://upgrade.actiontec.com/
https://controlpanel.tzo.com/cgi-bin/tzopanel.exe
https://upgrade.actiontec.com/MI424WR2/MI424WR2.rmt
https://cpe-ems79.verizon.com/cwmpWeb/CPEMgt
OpenRG Features
I was going through some of the new features advertised in Jungo's OpenRG software (which apparently is installed on my new router). These features stuck out:
NationZone (Guest Access) An end-to-end service, which enables Operators to convert their deployed residential gateways into a nation wide hotspot network, providing their customers with a Wifi roaming network without adding infrastructure costs
Video Surveillance Jungo has added a video surveillance service to Jungo.net. End users can subscribe to this service and can securely and remotely use multiple IP cameras that are connected to their home or office gateway
huh... "Enable operators (read ISPs) to convert .... into a nation wide hotspot"
NationZone (Guest Access) An end-to-end service, which enables Operators to convert their deployed residential gateways into a nation wide hotspot network, providing their customers with a Wifi roaming network without adding infrastructure costs
Video Surveillance Jungo has added a video surveillance service to Jungo.net. End users can subscribe to this service and can securely and remotely use multiple IP cameras that are connected to their home or office gateway
huh... "Enable operators (read ISPs) to convert .... into a nation wide hotspot"
Friday, July 24, 2009
Building a MIPS64 cross compiler
./configure --prefix=/usr/local/mips64-elf --target=mips64-elf --with-gnu-as --with-gnu-ld --enable-languages=c,c++ --program-prefix=mips64-elf-
checking build system type... i686-pc-linux-gnu
checking host system type... i686-pc-linux-gnu
...
checking build system type... i686-pc-linux-gnu
checking host system type... i686-pc-linux-gnu
...
OpenRG
Once you have a busybox shell you can basically do anything. I'm eventually gonna build a mips64 cross compiler so I can put some other tools on board, but that takes time...something I don't have a lot of....
Here's the loaded module list for those interested in what this router is running:
/proc # cat version
Linux version 2.6.16.14 #1 SMP Wed Mar 4 01:29:00 PST 2009
And loaded modules…
/proc # lsmod
Module Size Used by
clnkdvr 220688 0
ks8995m_mod 11728 0
dwc_otg 141568 0
octeon_eth 44536 0
wlan_scan_ap 6672 0
qos_ingress 3584 0
btn 5568 0
rg_pppoe_relay 6752 0
pppoe_relay 168544 1 rg_pppoe_relay
kleds_mod 7392 0
rg_ipv4 3584 0
rg_dhcp_pktfil 8720 0
tcp_mss 5008 0
rg_stp 16656 2
igmp_proxy_mod 37456 1
log_chardev 5936 0
ath_pci 109360 0
wlan_acl 5504 0
wlan_xauth 2816 0
wlan_ccmp 9216 0
wlan_tkip 13696 0
wlan_wep 7296 0
ath_dfs 34192 1 ath_pci
ath_rate_atheros 30208 1 ath_pci
wlan 166432 9 wlan_scan_ap,ath_pci,wlan_acl,wlan_xauth,wlan_ccmp,wlan_tkip,wlan_wep,ath_rate_atheros
ath_hal 224208 3 ath_pci,ath_rate_atheros
one_module 826832 23 ks8995m_mod,qos_ingress,btn,rg_pppoe_relay,kleds_mod,rg_ipv4,rg_dhcp_pktfil,tcp_mss,rg_stp,igmp_proxy_mod,log_chardev
Here's the loaded module list for those interested in what this router is running:
/proc # cat version
Linux version 2.6.16.14 #1 SMP Wed Mar 4 01:29:00 PST 2009
And loaded modules…
/proc # lsmod
Module Size Used by
clnkdvr 220688 0
ks8995m_mod 11728 0
dwc_otg 141568 0
octeon_eth 44536 0
wlan_scan_ap 6672 0
qos_ingress 3584 0
btn 5568 0
rg_pppoe_relay 6752 0
pppoe_relay 168544 1 rg_pppoe_relay
kleds_mod 7392 0
rg_ipv4 3584 0
rg_dhcp_pktfil 8720 0
tcp_mss 5008 0
rg_stp 16656 2
igmp_proxy_mod 37456 1
log_chardev 5936 0
ath_pci 109360 0
wlan_acl 5504 0
wlan_xauth 2816 0
wlan_ccmp 9216 0
wlan_tkip 13696 0
wlan_wep 7296 0
ath_dfs 34192 1 ath_pci
ath_rate_atheros 30208 1 ath_pci
wlan 166432 9 wlan_scan_ap,ath_pci,wlan_acl,wlan_xauth,wlan_ccmp,wlan_tkip,wlan_wep,ath_rate_atheros
ath_hal 224208 3 ath_pci,ath_rate_atheros
one_module 826832 23 ks8995m_mod,qos_ingress,btn,rg_pppoe_relay,kleds_mod,rg_ipv4,rg_dhcp_pktfil,tcp_mss,rg_stp,igmp_proxy_mod,log_chardev
BusyBox is now Available

Wow, I can't believe how much access one has to this router. Turns out busybox is available on the telnet port.
telnet 172.16.0.4
Trying 172.16.0.4...
Connected to 172.16.0.4.
Escape character is '^]'.
Username: root
Password:
Wireless Broadband Router> system
system> shell
Temporary setting log_level off
BusyBox v1.01 (2005.09.07-07:38+0000) Built-in shell (lash)
Enter 'help' for a list of built-in commands.
Look at /proc/cpuinfo
cd /proc
/proc # cat cpuinfo
system type : MC524WR
processor : 0
cpu model : Cavium Networks Octeon CN50XX V0.1
BogoMIPS : 1000.47
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes
ASEs implemented :
VCED exceptions : not available
VCEI exceptions : not available
processor : 1
cpu model : Cavium Networks Octeon CN50XX V0.1
BogoMIPS : 1000.47
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes
ASEs implemented :
VCED exceptions : not available
VCEI exceptions : not available
This is quite a powerful little router. Dual core Octeon 64 bit processors running at 1Ghz.
Ok Check This Out
Via the web interface of the ActionTec router there is a configuration file you can dump. Not knowing what was in it, I decided to dump the config and read through it. HOLY CRAP....
In the config you can see the user name and password of the account that has access to port 4567:
(username(verizonfios))
(password(&cc;Ya&b9;&ae;&19;]&d1;&be;&ba;v))
I could also see the username and password for the Admin account which I changed for this blog temporarily so you could see an example hash with plaintext password (hoping that someone smart can break it, it's probably dirt simple)
(username(root))
(password(&97;50&91;u&ea;0∾&86;|4m&cb;2&a9;&e4;))
Password is AAAAAAAA11111111
I thought on a whim that the password for the verzionfios might be on the web somewhere.....(really hoping NOT)...BOOM here it is (confirmed by my friend)
http://filedb.experts-exchange.com/incoming/2008/06_w23/30839/Wireless-Broadband-Router.txt
So this is messed up, the secret backdoor port 4567 has the same username and password enabled for every router. Nice...just waiting for FIOS networks to become the WORLDS LARGEST, FASTEST BOTNETS.
In the config you can see the user name and password of the account that has access to port 4567:
(username(verizonfios))
(password(&cc;Ya&b9;&ae;&19;]&d1;&be;&ba;v))
I could also see the username and password for the Admin account which I changed for this blog temporarily so you could see an example hash with plaintext password (hoping that someone smart can break it, it's probably dirt simple)
(username(root))
(password(&97;50&91;u&ea;0∾&86;|4m&cb;2&a9;&e4;))
Password is AAAAAAAA11111111
I thought on a whim that the password for the verzionfios might be on the web somewhere.....(really hoping NOT)...BOOM here it is (confirmed by my friend)
http://filedb.experts-exchange.com/incoming/2008/06_w23/30839/Wireless-Broadband-Router.txt
So this is messed up, the secret backdoor port 4567 has the same username and password enabled for every router. Nice...just waiting for FIOS networks to become the WORLDS LARGEST, FASTEST BOTNETS.
The solution
Well, being slightly paranoid and not wanting arbitrary folks logging into my router, I wanted to find a way to protect myself. I also thought the router manufacturer or ISP employees may give out the admin password for this strange port, then it hits the intert00bs and catastrophe...you know, cats and dogs blah blah.
So here's what you need to do if you own one of these routers:
1. Remove the router.
2. Remove the COAX conection from the ONT (Optical Network Connection)
3. Call your ISP and have then enable the Ethernet connection in the ONT.
4. Connect your favorite router to the Ethernet broadband ONT connection
5. Put the ISP's router behind your router
6. Keep the COAX connection from the ISPs router to the STB (Set Top Box) to maintain program information and monitoring of what you watch…..(or just leave it disconnected and use your TIVO, MythTV etc. for program information)
That doesn't turn the port off but at least makes it hard to get to from the outside. Time to do some deeper investigation.
So here's what you need to do if you own one of these routers:
1. Remove the router.
2. Remove the COAX conection from the ONT (Optical Network Connection)
3. Call your ISP and have then enable the Ethernet connection in the ONT.
4. Connect your favorite router to the Ethernet broadband ONT connection
5. Put the ISP's router behind your router
6. Keep the COAX connection from the ISPs router to the STB (Set Top Box) to maintain program information and monitoring of what you watch…..(or just leave it disconnected and use your TIVO, MythTV etc. for program information)
That doesn't turn the port off but at least makes it hard to get to from the outside. Time to do some deeper investigation.
Port 4567
time to go spelunking

A while ago I had set up a TrixBox and knew that I'd have to dig into this new Fios router to re-enable my phone service (I'm a geek, I have cisco phones throughout the house). The Fios installer was kind enough NOT to leave the router admin account/password with me, so I had to search the web to find it LOL. Anyway once logged in I'm presented with a fairly ghay interface which hurts my eyes. I enabled port forwarding for SIP and RTP and got my TrixBox working again. While I was poking around I noticed this interesting port forward rule that YOU CAN'T TURN OFF!!!
The Router from my favorite FIOS provider


I got this new router with my snazzy FIOS service. It's made by actiontec and seems to be a pretty powerful unit. By default, at least in my area, the ISP connected the COAX side of the router to their ONT (Optical Network Terminal) which usually sits just outside your house by the phone lines. On the inside they split the COAX, one side goes to your STB (Set Top Box), and the other to your router. The router uses the MOCA (Multimedia over Coax Alliance) protocol on the COAX line to get intelligent networking to your STB (so it can get program updates...kinda like Tivo).
Subscribe to:
Comments (Atom)